Oblivious Transfer: The cornerstone of MPC
From basics to extension
to help others discover it! 🥰
Table of Contents
Oblivious transfer#
Oblivious transfer (OT) is a basic two-party cryptographic protocol between a sender, who holds a collection of messages, and a receiver, who wants to obtain some of them. In an OT, the receiver picks exactly which messages to learn but learns nothing about the others and the sender learns nothing about the receiver’s choice. Common flavors are:
- 1-out-of-2 OT, where the sender has two messages and the receiver picks one;
- 1-out-of-m OT, where the sender has messages and the receiver picks one;
- n-out-of-m OT, where the receiver picks any of the sender’s messages.
The choice of n and m depends entirely on the application’s needs.
For example, imagine the sender has answers to 10 multiple-choice questions, and the receiver only wants the answer to question 3. OT lets them get that one answer, without the sender knowing which question they asked about, and without learning anything about the other 9 answers.
OT variants#
The simplest type of OT is 1-out-of-2, where the sender has two messages, and the receiver picks one of them. There are several useful variations of this basic form:
- Standard OT (Chosen-message OT): The sender chooses both messages, and , and the receiver selects one ( for some bit ) without revealing their choice.
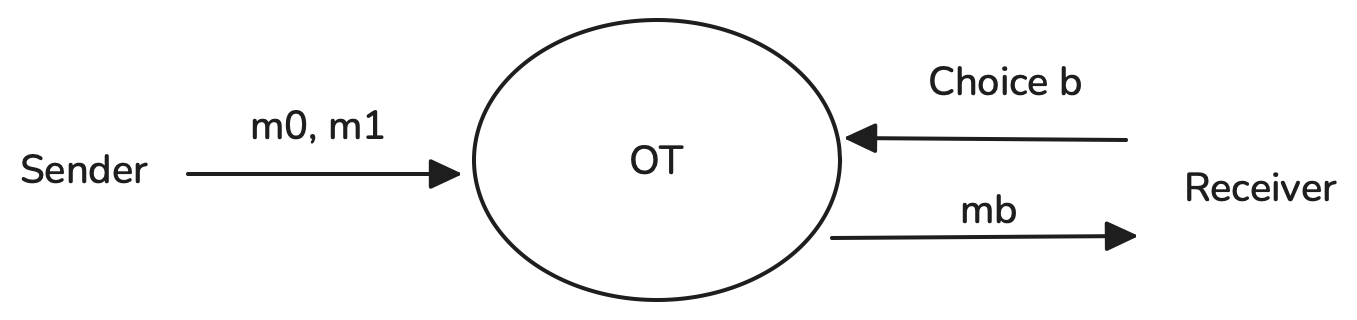
- Random OT (ROT): The two messages and are not chosen by the sender. Instead, the protocol itself generates them at random, and both the sender and receiver learn only their respective parts. This is often used as a building block for more advanced protocols.
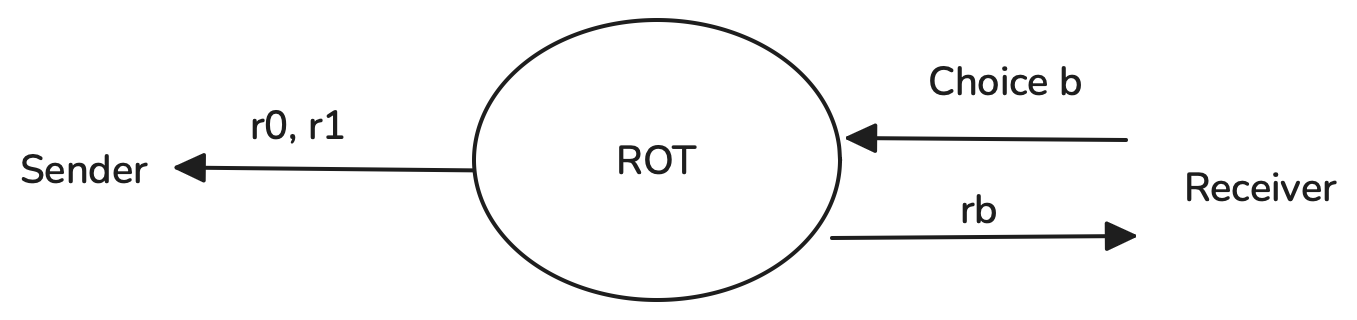
- Correlated OT (COT): The sender does not choose two completely independent messages. Instead, they choose one message , and the second is computed as , where is a fixed correlation value. The receiver still learns only one of the two.

- Random Correlated OT (RCOT): Like COT, the two messages are correlated using a value , but here is generated randomly by the protocol itself rather than chosen by the sender. So the pair looks like , where is a random value.
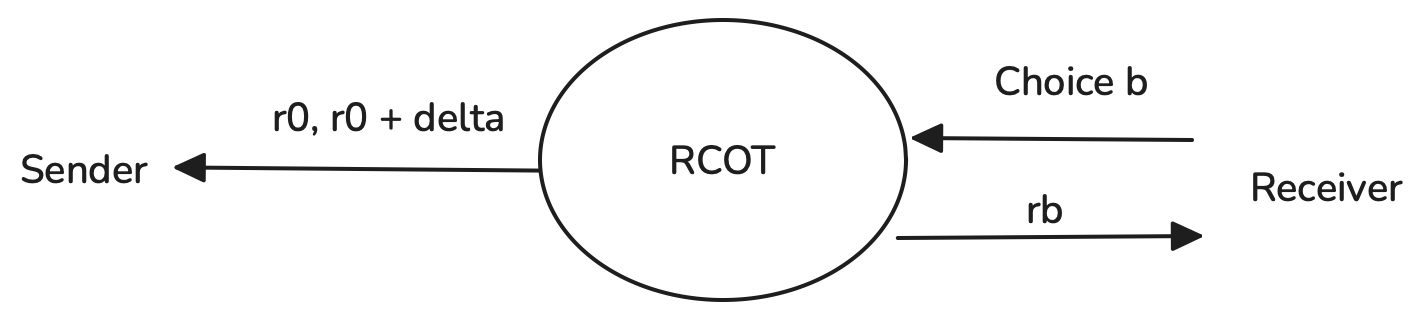
These variants are especially useful in practice, particularly in efficient implementations of OT extension (discussed later), where generating many lightweight OTs with specific properties is needed.
Security Models for OT#
The security of an Oblivious Transfer protocol is defined by the type of adversary it can defend against. Different protocols offer different levels of assurance, which fall into two main categories:
- Semi-Honest (or Passive) Security: It assumes both parties follow the protocol's instructions exactly but may try to learn extra information by analyzing the messages they receive. A protocol secure in this model guarantees that an honest-but-curious party learns nothing beyond what they are entitled to.
- Malicious (or Active) Security: This is a much stronger model that assumes an adversary can deviate from the protocol in any way they choose. They can send malformed messages, use inconsistent inputs, or abort prematurely to try and break the security. A maliciously secure protocol guarantees that an honest party is always protected: either the protocol completes correctly with all secrets intact, or the honest party detects the cheating and aborts, preventing any security breach.
These distinctions are crucial, as foundational protocols like basic OT extensions are often designed for the semi-honest model, while more advanced versions add specific checks to provide robust security against malicious adversaries.
Base OT#
Base OTs are a small number of 1-out-of-2 Oblivious Transfers that are run at the setup phase of larger protocols, such as OT extension. They are called “base” because they provide the secure foundation from which many more lightweight OTs can be generated. Base OTs are considered computationally expensive as they typically rely on public-key cryptography such as elliptic curve operations or modular exponentiation which are slower than symmetric cryptographic operations. However, only a small number of base OTs are needed, so this cost is acceptable in practice. Once the base OTs are completed, the parties can use them to securely derive thousands or millions of fast OTs using only efficient symmetric cryptography (ex: AES).
A widely used protocol for base OT is the Chou-Orlandi protocol (2015), which is optimized for speed and low communication overhead.
Chou-Orlandi#
The Chou-Orlandi protocol is an efficient implementation of 1-out-of-2 chosen-message Oblivious Transfer (OT) based on elliptic curve cryptography. It is designed to be fast and easy to batch, which makes it widely used in practice. A batched version of this protocol is implemented in the MPZ library.
In this protocol, the Sender holds two messages and wants to send exactly one of them to the Receiver, depending on the Receiver’s choice bit, without learning which message was chosen. To achieve this, the protocol derives two shared secret keys through an Elliptic Curve Diffie-Hellman (ECDH) style exchange: one key corresponds to each message.
The Sender uses these keys to encrypt (mask) their two messages, while the Receiver can only derive the key matching their choice bit and thus decrypt only their selected message. This ensures the Receiver learns nothing about the unchosen message, and the Sender learns nothing about the Receiver’s choice.
Although it’s a chosen-message OT, it can be easily adapted into Random OT (ROT) by treating these derived encryption keys as the random messages themselves.
At a high level, the protocol is built on the principles of ECDH key exchange:
Let:
- be the base point of an elliptic curve
- , be random private scalars chosen by the Sender and Receiver, respectively
- be the receiver’s choice bit
-
Sender’s setup: The sender picks a random private key and computes their public key:
-
The Receiver sends to the receiver his public key , based on his choice bit :
- if
- if
-
The Sender computes both keys:
Using their private key and the received public key , the sender computes:
These are used as symmetric keys to encrypt messages
-
The Receiver computes a single key using his secret :
This match exactly one of or depending on . The receiver can decrypt one message, but gains no information about the other.
Let’s see what values the sender computes, and why only one matches the receiver’s key.
- if :
- Receiver computes
- Sender computes
- if :
- Receiver computes:
- Sender computes:
In both cases, only one key matches, depending on the receiver's choice and the sender cannot tell which one.
A full implementation can be found in MPC by hand
OT extensions#
As discussed earlier, base OTs are expensive because they rely on public-key cryptography, which makes generating millions of them impractical.
OT extensions solve this by allowing two parties to efficiently generate a large number of OTs using only a small number of base OTs, followed by fast symmetric-key operations. These protocols work in two main steps:
- Initialization: Perform a small, fixed number of base OTs using public-key cryptography (like Chou Orlandi). The outputs act as shared seeds.
- Extension: Use those seeds to generate many more OTs, thousands or even millions, using only symmetric primitives.
The most widely used OT extension protocol is IKNP, which is secure in the semi-honest model.
For stronger security against actively malicious parties, the KOS protocol extends IKNP with additional checks to detect cheating.
IKPN#
The IKNP protocol is an efficient OT extension that lets two parties generate a large number of 1-out-of-2 OTs using only a small number of expensive base OTs. It operates in the semi-honest model, where both parties follow the protocol but may try to learn additional information.
The key idea is to use symmetric encryption (ex: hash functions) to mask each message so that:
- The receiver can only decrypt one message based on their choice bit.
- The sender learns nothing about that choice.
A clever trick in IKNP is a role reversal during the base OTs:
- The party who is the sender in the final OTs (we’ll call her Alice) acts as the receiver in the base OTs.
- The party who is the receiver in the final OTs (we’ll call him Bob) acts as the sender in the base OTs.
This swap allows them to establish correlated data that both can later use to derive the right symmetric keys for the actual OTs. Here is a high level overview:
sequenceDiagram
participant Alice
participant Bob
rect rgb(240, 255, 245)
Note right of Alice: Base OT Phase
Bob->>Alice: sends tᵢ, tᵢ ⊕ r
Alice-->> Bob: choose one
end
Note right of Alice: Role Reversal
rect rgb(240, 240, 255)
Note right of Alice: Final OT Phase
Alice->> Bob: sends encrypted messages (m0_i, m1_i)
Bob-->> Alice: chooses one message to decrypt
end
-
The setup
Alice inputs: pairs of messages of length bits
Bob inputs: a choice bit vector
-
Bob (Receiver in final OT) builds inputs for base OT
- Bob generate a matrix and construct inputs of the base OT like:
- Bob acts as the sender in
kbase OTs, using each pair as the two possible messages.
-
Alice (sender in final OT) participates in base OT
- Alice generate a random bit vector
- She acts as the receiver in the base OTs with choosing bit in each.
- After the base OT, Alice will have received vectors of length and can construct the matrix of size that satisfy for each columns:
We can rework this equation into:
Where is Alice’s bit vector and is Bob’s choice bit for row . The base OT is now finished.
-
Now Alice wants to send and to Bob in a way that:
- Bob can decrypt only one of them (based on )
- Alice doesn’t know which one
For each OT index :
- Alice computes two keys: She uses there to encrypt:
- Bob computes: He then decrypts:
This works because the key values align depending on Bob's bit :
- if :
- Alice has:
- Bob computes:
- if
- Alice has:
- Bob computes:
So Bob always gets exactly one key matching his choice, and Alice can’t tell which one he used.
A full implementation can be found in MPC by hand.
KOS#
KOS15 is a security-hardened improvement of the IKNP protocol, designed to defend against malicious receivers in OT extension. It provides the same functionality generating many 1-out-of-2 OTs from a small number of base OTs but strengthens guarantees when parties might not follow the protocol honestly. The IKNP protocol works well in the semi-honest model, where both parties are assumed to follow the protocol honestly, even if they try to learn more from the messages they receive. But in the malicious model, where a party might arbitrarily deviate from the protocol to gain information, IKNP is vulnerable.
Specifically, a malicious receiver (Bob) can exploit the base OT phase, where the roles are reversed (i.e., Bob acts as the sender). Here's how the attack works:
Bob wants to learn Alice’s secret correlation vector , which she uses to compute the OT masking keys. If Bob learns he can decrypt both messages in future OTs, completely breaking OT security.
In the base OT phase of IKNP, for each column of the matrix , Bob is supposed to send a pair of messages: where:
- is a random vector
- is Bob’s choice vector, used consistently across all columns
However, if Bob is malicious, he can cheat by using a different per column:
Suppose Bob wants to learn (the first bit of Alice's secret vector ). He can:
-
In column 1, use the vector: That is, only the first row has a 1, the rest are 0.
-
This means the pair he sends becomes:
-
When Alice selects either or depending on her bit , she gets:
So:
Bob knows , so by comparing what Alice eventually encrypts using , he can deduce .
Later, in the extension phase, Alice sends two encrypted messages:
If Bob knows (or guesses) either or , he can invert the hash and recover . Repeating this attack over all columns lets Bob reconstruct the full secret . Once Bob knows , he can derive both keys and in the final OT round:
- Decrypt both messages
- Break sender’s privacy
- Undermine the security of all protocols relying on OT
This is a critical failure, and exactly what KOS15 was designed to prevent.
To prevent this, KOS15 adds a correlation check step after the IKNP base phase. This check ensures that the receiver used a single, consistent choice vector , without allowing them to tamper column-wise.
We will focus on the MPZ implementation of KOS15 which omits the final randomization phase (needed only for ROT) and uses the optimized IKNP base from ePrint 2016/602. We suppose you have knowledge of the IKNP protocol.
- The setup (modified IKNP): Alice and Bob execute the IKNP protocol up to but not including the final message hashing and output step. At the end both hold matrices:
- Bob:
- Alice:
- Their rows satisfy:
- is Bob’s choice bit
- is Alice’s hidden correlation string
- The correlation check: to confirm that Bob used a single consistent x, a random linear check is performed.
- Bob (Receiver) computes: where are random challenge bits (agreed by both parties). Bob sends to Alice
- Alice (Sender) computes: If the equation holds: continue with OT If the check fails, it aborts: it means Bob tried to cheat. This check ensures that Bob committed to a single vector across all columns, preventing the column-wise cheating attack possible in IKNP.
If random OT is desired (for use in correlated or random protocols), an additional randomization phase is required. The MPZ version skips this step.
An example of MPZ implementation is available MPC by hand