Stay in Range: Deeper Into Bulletproofs
to help others discover it! 🥰
Table of Contents
We previously saw how the Bulletproofs Inner Product Argument (IPA) works: it lets us prove that we know a secret vector without revealing it.
That’s neat, but what can we actually do with it?
→ Range proofs!
Bulletproofs are the backbone of modern range proofs: they allow us to prove that a secret value lies within a given range, without revealing the value itself.
Don’t worry if you haven’t read the previous IPA articles, you can think of the IPA as a black box that proves an inner product relation without exposing the vectors. Though… if you do want to understand it, go read Breaking Down Bulletproofs (part 1) and Unfolding the Bulletproofs Magic (part 2).
Here’s a quick overview of what we’ll go through today 😅
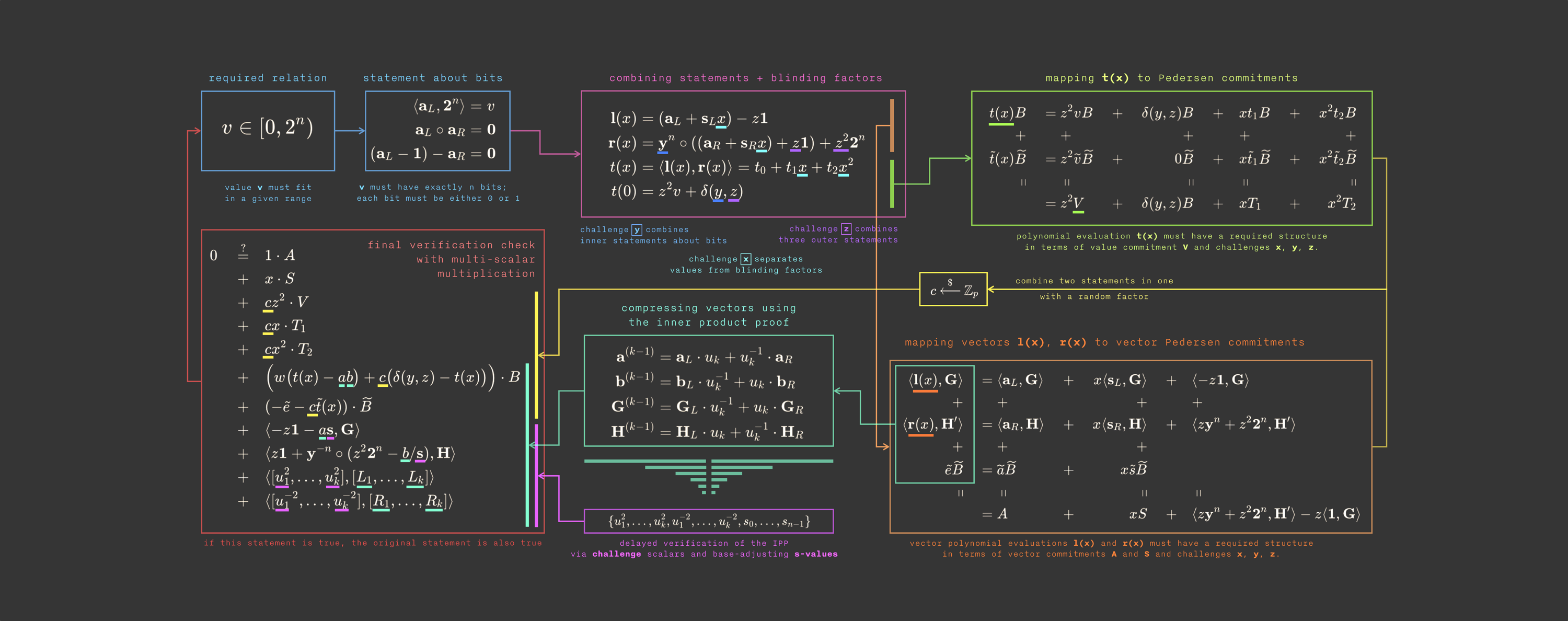
(this diagram comes from the excellent Dalek Bulletproofs documentation)
Nooo! 🥲 Don’t stop here! I promise that by the end of this article, this strange-looking graph will make perfect sense.
A motivating example#
A great use case is confidential transfers.
Imagine you want to send money to a friend, but you don’t want anyone else to see how much. You still need to prove that the transfer makes sense: you’re not sending a negative amount or exceeding your balance.
In many privacy-preserving systems (for example, when balances are represented by homomorphic commitments), this requires proving that both the amount and the resulting balance stay within valid ranges, preventing overflows/underflows, without revealing their actual values.
For instance:
- the maximum amount you can transfer is 100
- the maximum balance allowed is 1000
You would produce two range proofs:
- Transfer amount is valid: 0 ≤ amount ≤ 100
- Resulting balance is valid: 0 ≤ balance - amount ≤ 1000
If both hold, your transfer is correct… without revealing the actual numbers.
These kinds of proofs are called range proofs, and Bulletproofs are one way to build them efficiently.
Other constructions exist too (see, for instance, the 2024 SoK paper), but Bulletproofs remain among the most practical today. They were famously adopted by Monero to enable confidential transactions in production.
What are we trying to prove?#
We want to prove that a secret value lies in the range , without revealing .
You can adapt the same logic to any range , but today I’ll keep powers of 2, it makes the math cleaner.
As you probably guessed, we’ll reuse our vector machinery and the Inner Product Argument we built earlier (need a refresher? checkout out Breaking Down Bulletproofs (part 1) and Unfolding the Bulletproofs Magic (part 2) 😁).
Notations#
Whenever I use bold, it means I’m talking about a vector.
vector of length n of successive powers of 2
vector of n zeros
vector of n ones
vector of length n of successive powers of a random value y
vector n elements, all equal to z ( scaled by )
Breaking our secret number into bits#
The key trick in Bulletproofs range proofs is bit decomposition, breaking a secret number into its individual bits.
This is the same basic approach used in other systems as well: you prove that each bit is either 0 or 1, and that their weighted sum reconstructs the value. In Circom, for example, this is done with the Num2Bits gadget.
Although newer proving systems sometimes use lookup-based range checks for efficiency, bit decomposition remains the fundamental building block that most protocols rely on.
We represent the secret value as a sum of its bits.
Let be the vector of bits of .
For example, if :
Then:
That inner product expresses exactly how binary numbers work:
(note: here i’m assuming that is in little endian)
With our example (in big-endian form):
Our range proof will revolve around convincing the verifier that:
- this equation holds, and
- each really is a bit (0 or 1)
That’s important because the verifier will only ever see a commitment to , not the vector itself. So without this check, the prover could hide arbitrary values inside the commitment and still make the equations balance.
Convincing the verifier our bits are real 0s and 1s#
We can’t just tell the verifier our bits, that would reveal .
So we need a way to prove that every component of is either 0 or 1.
For a single number , being a bit means:
Only if is 0 or 1 does the equation hold.
For vectors, we use element-wise (Hadamard) multiplication :
So we define a new vector:
and we want to prove that:
which ensures that all entries of are binary.
You might wonder why we introduce a new vector instead of just using directly in the equation.
The reason is mostly structural: we need to refer to both and in different parts of the proof, sometimes together and sometimes separately.
By assigning this expression to its own variable, we make later equations cleaner and easier to work with, especially when we start building inner products and commitments involving each vector independently. Each vector plays a different role in the proof, and defining them explicitly ensures those commitments remain consistent with the constraints we’re enforcing.
You can also think of it as a circuit, where each operation produces a new variable and we constrain each relation.
In pseudocode, that would look like:
def range_proof_circuit(params, priv, pub): bitlen = params com_v = pub a_L, a_R, ... = priv assert com(sum(a_L * power_of_2)) == com_v assert a_R == a_L - vec_1 assert a_L * a_R == vec_0
A clever probabilistic trick#
How can we prove that two hidden vectors multiply to zero without revealing them?
We start with a simple intuition: suppose you want to prove that a secret number equals 0.
If the verifier gives you a random value , and you respond with
(we suppose you can’t cheat, and have to send the actual result of that product)
then unless you’re (really) lucky, the only way that can hold is if .
We apply the same idea to vectors, but there’s a subtle difference…
Schwartz–Zippel for inner-product
We just saw how a random challenge can help check that a single value equals zero.
Here, we actually have several equations (one per vector element) that we want to hold simultaneously:
If this isn’t the case, the terms could cancel each other out.
For example, with a vector of length 3, you could have:
Even though each row is nonzero, their sum (the inner product) equals 0, which is not what we want.
To avoid that, we add randomness to each row.
This way, even if you try to cheat, you can’t predict how to make the terms cancel.
The verifier sends a random vector of length , and the prover must now show:
Why does this work?
Because the random coefficients in act as independent scalings for each term, so any potential cancellations become essentially impossible.
If this equality holds for a random challenge , it’s overwhelmingly likely that the element-wise products themselves are all zero.
Formally, this relies on the Schwartz–Zippel lemma: we treat the left-hand side as a polynomial and test whether it evaluates to zero at a random point. If it does, it’s very likely that the whole polynomial is identically zero, and the probability of being fooled is at most .
To reduce communication, the verifier doesn’t send the whole vector , but just a single random value .
The prover then constructs
is correctly formed#
We have one last issue… we also need to show that was defined honestly:
Easy! We do this by proving another inner product equals zero:
Again, because the verifier choses randomly, the prover can’t fake it.
Recap: everything we must prove#
In summary, the prover needs to prove three relations, each reduced to an inner product that can be verified using the IPA:
Notice that I slightly rearranged the third equation.
It’s equivalent to what we had before:
but the structure of the equation now aligns better with how Bulletproofs commitments are expressed later on.
That’s our full setup! From here, we’ll move on to the heavier algebra that ties everything together.
Combining inner products#
So far, we have three separate inner products to prove.
That’s quite a bit to handle.
Ideally, we’d like to bundle them into one single inner product that can be proven with a single IPA.
To do that, we introduce another random challenge from the verifier: .
Then we take a random linear combination of the three equations using powers of :
That way, the prover can’t “tune” each equation independently to cheat. Everything must be consistent across the combination.
We now want to rearrange this equation so that:
- the left part of the inner product is only a function of
- the right part depends only on
- the result depends only on , and constants known to the verifier
That clean separation will make it much easier to later commit to each side independently.
First expand:
Then move to the other side, and move into the inner products:
Finally group by and
Now add the same term to both sides:
After simplifying, we obtain:
Every term on the right-hand side (except ) is known to the verifier, so we can group them into a single known value , which only depends on the random challenges:
And with that, we finally get the single inner product we’ll work with going forward:
We’ve now combined all three constraints into one compact inner product.
The random challenge ties them together so that the prover can’t selectively satisfy one and not the others.
This equation is the exact form we’ll use in the next step, when we blind and commit to the vectors.
SageMath setup#
Before going further, let’s add a bit of code.
From now on, I’ll use short SageMath snippets to illustrate each step of the proof.
We’ll work over a tiny toy field to keep computations simple (real systems use large 256-bit fields).
Specifically, we’ll use:
- the prime field ,
- the elliptic curve over that field: , which has a prime order 919
p = 929
Fp = GF(p)
E = EllipticCurve(Fp, [5, 15])
Fr = GF(E.gens()[0].order())
The goal is to check that is 8 bits
We define the vectors:
and then decompose into bits to form , and
n = 8 # number of bits
print(f"We will be proving that v is between 0 and {pow(2, n)}\n")
# (2^0, 2^1, 2^2, ..., 2^(n-1))
vec_2n = vector([Fr(2 ^ i) for i in range(n)])
# (1, 1, 1, ..., 1)
vec_1n = vector([Fr(1)] * n)
v = Fr(random.randint(0, pow(2, n)))
print("v =", v)
v_bin = bin(v)[2:].zfill(n)[::-1][:n]
print("v_bin = ", v_bin)
aL = vector([Fr(int(bit)) for bit in v_bin])
assert v == sum([aL[i] * 2 ^ i for i in range(n)])
assert v == inner_product(aL, vec_2n)
# Define aR
aR = aL - vec_1n
assert inner_product(aL, aR) == 0
print("aL = ", aL)
print("aR = ", aR)
This matches our earlier equation:
The core proof (without zero-knowledge)#
If we stopped here, we could already run an Inner Product Argument (IPA) on our combined inner product and get a valid proof, just like in the previous article 😊.
But there’s a problem: the IPA is not hiding. It would reveal information about the witness, possibly leaking the secret value .
In the real protocol, we’ll fix this using blinding vectors .
Before getting there, let’s strip things down and see how a simplified version, without any blindings, would work.
We start from the previously combined relation, and name these two sides of the inner product:
A completely naive protocol would have the prover just send and prove that
But that’s neither binding nor private. Anyone could fake vectors that satisfy the equation.
So we add commitments.
Commit#
At the start of the protocol (before knowing ), the prover commits to the bit vectors and the value :
Here:
- and are vectors of elliptic-curve generators (one per bit of )
- are single generators, for scalar commitments
- are random scalars used for hiding (blinding factors)
# Define generators
G = E.random_point()
H = E.random_point()
Gs = [E.random_point() for _ in range(n)]
Hs = [E.random_point() for _ in range(n)]
# Commit to v
print("\nWe can commit to v from the start")
blinding_gamma = Fr.random_element()
V = v * G + blinding_gamma * H
print(f"v commitment (V): {V}\n")
blinding_alpha = Fr.random_element()
A = inner_product(aL, Gs) + inner_product(aR, Hs) + blinding_alpha * H
print("A = ", A)
print("\nProver sends A, V to Verifier")
Then the verifier sends the challenges
print("Verifier sends random challenges y and z\n")
y = Fr.random_element()
vec_y_n = vector([y ^ i for i in range(n)])
z = Fr.random_element()
vec_z_1n = vector([z] * n)
So we can now define our main relation
l = aL - vec_z_1n
r = aR.pairwise_product(vec_y_n) + vec_y_n * z + z ^ 2 * vec_2n
main_inner_product = inner_product(l, r)
delta_y_z = (z - z ^ 2) * inner_product(vec_1n, vec_y_n) - z ^ 3 * inner_product(vec_1n, vec_2n)
t = z ^ 2 * v + delta_y_z
assert main_inner_product == t
print("Combined inner product = z ^ 2 * v + delta_y_z.\nWe can continue...\n")
Rescaling the generators: #
The previous commitments are computed at the very start of the protocol, before receiving any challenge from the verifier.
Therefore, once the verifier sends the challenges , we face a subtle issue: contains powers of , but was created before was known.
Each coordinate of in the inner product is multiplied by , yet the commitment was made with plain . We need to reconcile these.
The trick is to absorb the factors into the bases. That’s why we define a new vector:
This rescaling ensures that, for any vector :
In other words, we can freely “move” the weights from the vector side to the generator side without changing the commitment.
vec_y_n_inv = vec_y_n.apply_map(lambda x: 1/x)
H_y_minus1 = [vec_y_n_inv[i] * Hs[i] for i in range(n)]
Build the point #
With this, the prover constructs a single elliptic curve point:
Using public information, the verifier can express in terms of the earlier commitments :
Let me show you this equality explicitly:
Perfect! Both representations of match.
P = A - inner_product(vec_z_1n, Gs) + inner_product(z * vec_y_n + z ^ 2 * vec_2n, H_y_minus1) - blinding_alpha * H
assert P == inner_product(l, Gs) + inner_product(r, H_y_minus1)
Inner Product Argument#
Finally the verifier needs to check that was constructed correctly, based on the values in his possession: , the challenges, and the public parameters.
Why does it work? Now that we understand , it’s easy:
IPA#
Finally, the prover runs an IPA with bases to prove that:
where:
- is yet another elliptic curve generator chosen by the verifier
The verifier:
- Reconstructs from via the formula above
- Verifies the IPA proof that
And that’s it! A fully sound but non–zero-knowledge range proof.
print("\nFinally we run the IPA with: P + t * Q")
Q = E.random_point()
ipa_proof = ipa(l, r, Gs, H_y_minus1, t, Q, Fr)
P_full = P + t * Q
verify(Gs, H_y_minus1, P_full, ipa_proof[0], ipa_proof[1], ipa_proof[2], ipa_proof[3], ipa_proof[4], Q, n, Fr)
print("IPA proof ✅")
To check the code for the ipa() function, see here: ipa.sage
And for the full script of our simplified protocol: range-proof-simple.sage
The real Bulletproof adds the missing blinding polynomials to make it private. But structurally, this is already the core of the protocol.
From now on, everything is about privacy… 🙈
Blinding for zero-knowledge: vectors to polynomials#
Up to now, we’ve combined our three inner products into one equation, and saw a non-zero-knowledge version of the protocol.
To make the proof zero-knowledge, we need to hide these vectors while still convincing the verifier that the relation holds.
The trick is twofold:
- introduce blinding factors to mask
- and move from vectors to polynomials, so we can combine real data and blinding terms in a single structured equation.
Let’s see how the prover builds these blinding polynomials and commits to them using Pedersen commitments, hiding all the secrets while keeping every equation verifiable.
Hiding our vectors with blinding terms#
The prover introduces two new random vectors: .
They act as noise to mask the real vectors: .
Using them, we define two polynomial vectors that depend on a variable :
When , these polynomials reveal the original expression we care about:
Now look at what happens when we take their inner product:
This is the core equation we ultimately want to prove.
By turning the vectors into polynomials, the prover can now safely reveal at one random point (chosen by the verifier) instead of revealing the full secret vectors.
Taking their inner product#
What happens when we take the inner product of two polynomial vectors?
If we have: and , then:
In other words, the result is a quadratic polynomial.
In our case, we call that polynomial :
The constant term is exactly our target inner product:
To compute the remaining coefficients efficiently, we can use a simple Karatsuba trick:
This saves some redundant work: instead of expanding everything term by term, we reuse the existing parts to derive the cross-term .
So from now on, our goals are:
- Prove that is correct: it equals
- Prove that is well formed:
- and are constructed correctly
Committing to everything#
Before the verifier can check anything, the prover must commit to all the relevant values. In a way that’s binding (he can’t change them later) but still hiding (the verifier learns nothing).
These commitments are made to elliptic-curve points and follow a strict order.
We already saw a lot of it when we previously described our “simplified protocol”, but it doesn’t hurt to get a reminder.
Step 1: commit to the secret value #
Using a random blinding factor :
where and are fixed, independent elliptic curve generators.
Step 2: commit to the bit vectors#
Now the prover commits to vectors and , and the blinding vectors and :
where:
- and are vectors of elliptic curve generators (one per bit of )
- and are blinding scalars
blinding_alpha = Fr.random_element()
A = inner_product(aL, Gs) + inner_product(aR, Hs) + blinding_alpha * H
print("A = ", A)
# blinding terms for left and right polys
sL = vector([Fr.random_element() for i in range(n)])
sR = vector([Fr.random_element() for i in range(n)])
blinding_beta = Fr.random_element()
S = inner_product(sL, Gs) + inner_product(sR, Hs) + blinding_beta * H
print("S = ", S)
print("\nProver sends A, S, V to Verifier")
Once and are committed, the verifier (or the Fiat-Shamir heuristic) can produce challenges and .
These are then used to define and .
R.<X> = Fr[]
lX = aL - vec_z_1n + sL * X
print("lX = ", lX)
rX = vec_y_n.pairwise_product(aR + vec_z_1n) + z ^ 2 * vec_2n + vec_y_n.pairwise_product(sR * X)
print("rX = ", rX)
tX = inner_product(lX, rX)
print(f"tX = {tX}\n")
Step 3: commit to #
Finally, the prover commits to the coefficients of : the linear and quadratic terms and , each with its own blinding factor :
These commitments make sure the prover can’t later tweak to make the equation magically work.
[t0, t1, t2] = tX.coefficients(sparse=False)
print("Notice that t0 is the inner product we're trying to prove\n")
assert t0 == main_inner_product
blinding_tau1 = Fr(123)
blinding_tau2 = Fr(456)
T1 = t1 * G + blinding_tau1 * H
T2 = t2 * G + blinding_tau2 * H
print("T1 = ", T1)
print("T2 = ", T2)
Putting it all together: verification#
Everything is almost ready! 🤩
The prover has committed to all the right pieces. Now the verifier just needs to check that everything lines up.
The final challenge#
The verifier sends one last random challenge .
By evaluating the polynomials and at this random point, we can check that the claimed relationships hold with overwhelming probability (thanks to the Schwartz–Zippel lemma).
The prover computes:
Here:
- is the evaluation of at , equal to the inner product of and
- combines all the blinding factors for
- combines the blinding factors for and
print("\nVerifier sends challenge x\n")
x = Fr.random_element()
print("x = ", x)
# evaluate left and right polys at u
lx = lX(x)
rx = rX(x)
tx = tX(x)
print("lx = ", lx)
print("rx = ", rx)
print("tx = ", tx)
assert tx == lx * rx
print("\nProver sends proof_blindings_mu and proof_blindings_tau to Verifier")
proof_blindings_mu = blinding_alpha + blinding_beta * x
proof_blindings_tau = z ^ 2 * blinding_gamma + blinding_tau1 * x + blinding_tau2 * x ^ 2
Verifier check #1: the polynomial #
First, the verifier ensures that matches the claimed polynomial evaluation .
Conceptually, it checks that:
and also that the commitment to is consistent with all earlier commitments.
The actual check is:
Why does this hold?
check1_lhs = tx * G + proof_blindings_tau * H
check1_rhs = V * z ^ 2 + delta_y_z * G + T1 * x + T2 * x ^ 2
assert check1_lhs == check1_rhs
print("Check 1 ✅")
Verifier check #2: vectors and #
Next, the verifier checks that the revealed vectors and are consistent with all previous commitments.
We already explained previously what is. But for the lazies, here it is again:
Then it computes:
and checks that:
If this equality holds, it means that the prover’s and were built correctly.
P = - proof_blindings_mu * H + A + S*x + inner_product(-vec_z_1n, Gs) + inner_product(z * vec_y_n + z ^ 2 * vec_2n, H_y_minus1)
print("P = ", P)
assert P == inner_product(lx, Gs) + inner_product(rx, H_y_minus1)
print("Check 2 ✅")
The Inner Product Argument: the final step#
But wait… the prover can’t just send full vectors and , that would reveal too much information.
This is exactly where the Inner Product Argument comes back in!
To prepare for it, we slightly rearrange the equation above:
and we the inner product result into it:
(where is a random elliptic curve point used for the IPA proof).
This is the input to the IPA: the prover produces a short recursive proof that .
In case you forgot, you can find our previous articles here: Breaking Down Bulletproofs (part 1) and Unfolding the Bulletproofs Magic (part 2).
Q = E.random_point()
print("Remember that tx = <lx,rx>")
ipa_proof = ipa(lx, rx, Gs, H_y_minus1, tx, Q, Fr)
P_full = P + tx * Q
verify(Gs, H_y_minus1, P_full, ipa_proof[0], ipa_proof[1], ipa_proof[2], ipa_proof[3], ipa_proof[4], Q, n, Fr)
print("IPA proof ✅")
What the final proof looks like#
The complete range proof includes:
- and
- and
- and its blinding factor
- (blinding for and )
- the IPA proof, which consists of:
- and vectors, from each folding step
- two scalars representing the final folded vectors and
And that’s it! we’ve just built a complete range proof from the ground up! 🧠
Starting from a simple idea: proving that a hidden value lies between 0 and , we combined a series of powerful tricks:
- Bit decomposition to express the value as a vector of 0s and 1s
- Random challenges () to tie every equation together and prevent cheating
- Commitments to hide the data while keeping all relationships consistent
- Blinding of inputs and outputs of IPA, as the IPA protocol is not zero-knowledge
- And finally, the Inner Product Argument to verify everything efficiently and compactly
All of that comes together so that a verifier can be convinced that: “the prover’s secret value lies in the correct range”, without learning anything about the value itself.
This foundation powers confidential transfers, private balances, and many other privacy-preserving systems, like the one we sketched at the start of this article.
You can find the entire Sagemath script here: range-proof.sage